Frontend
Summary
List of all rules
This page lists all the rules created for triggering alerts. You have a list that shows you multiple informations about each vulnerability of your network like the name, the date, the criticity and many usefull ones.
Rule Creation
When you click on the create button, you could choose between 3 rules types:
- Port
- Service
- Vulnerability
For the both lasts, you could create your rule basing on a regex or a specific service/vulnerability.
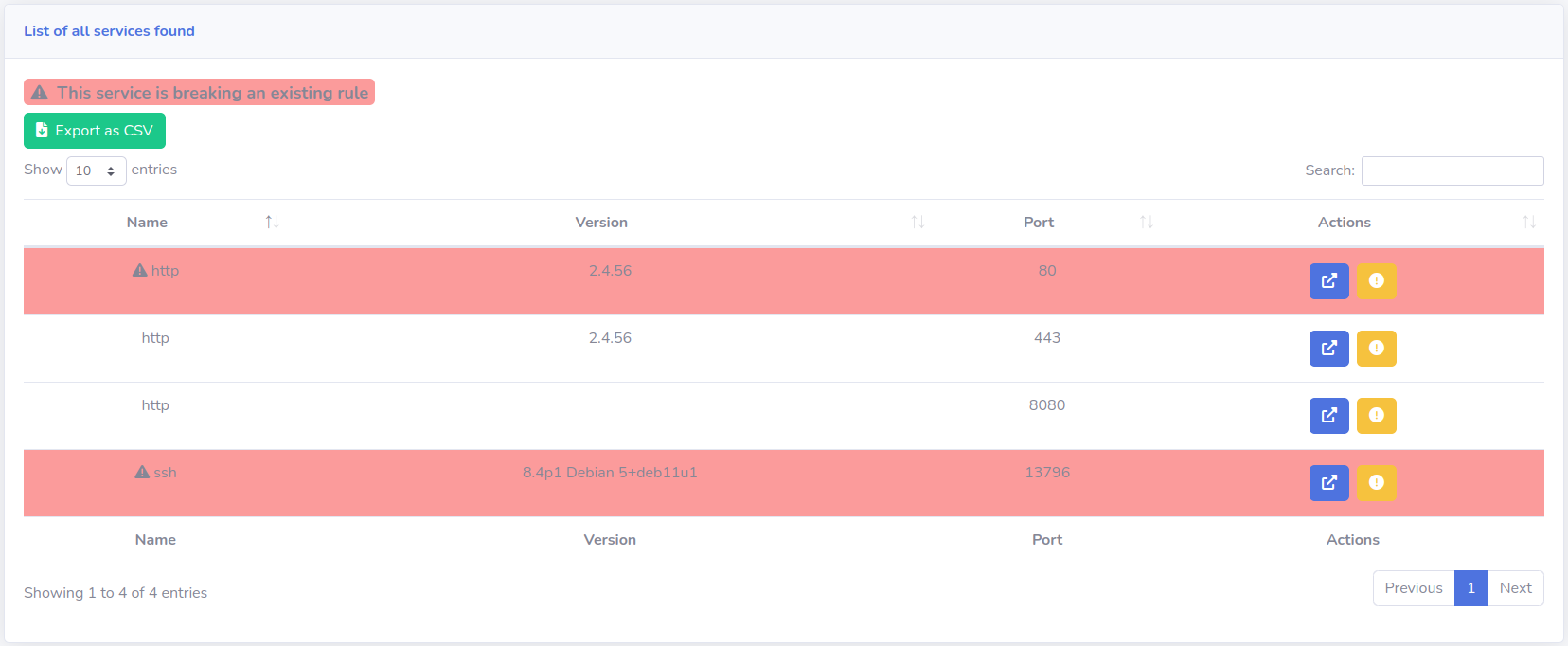
Rules Exploitation
For each matching rule, the line containing either the host, service or the vulnerability is higlighted with a red line.